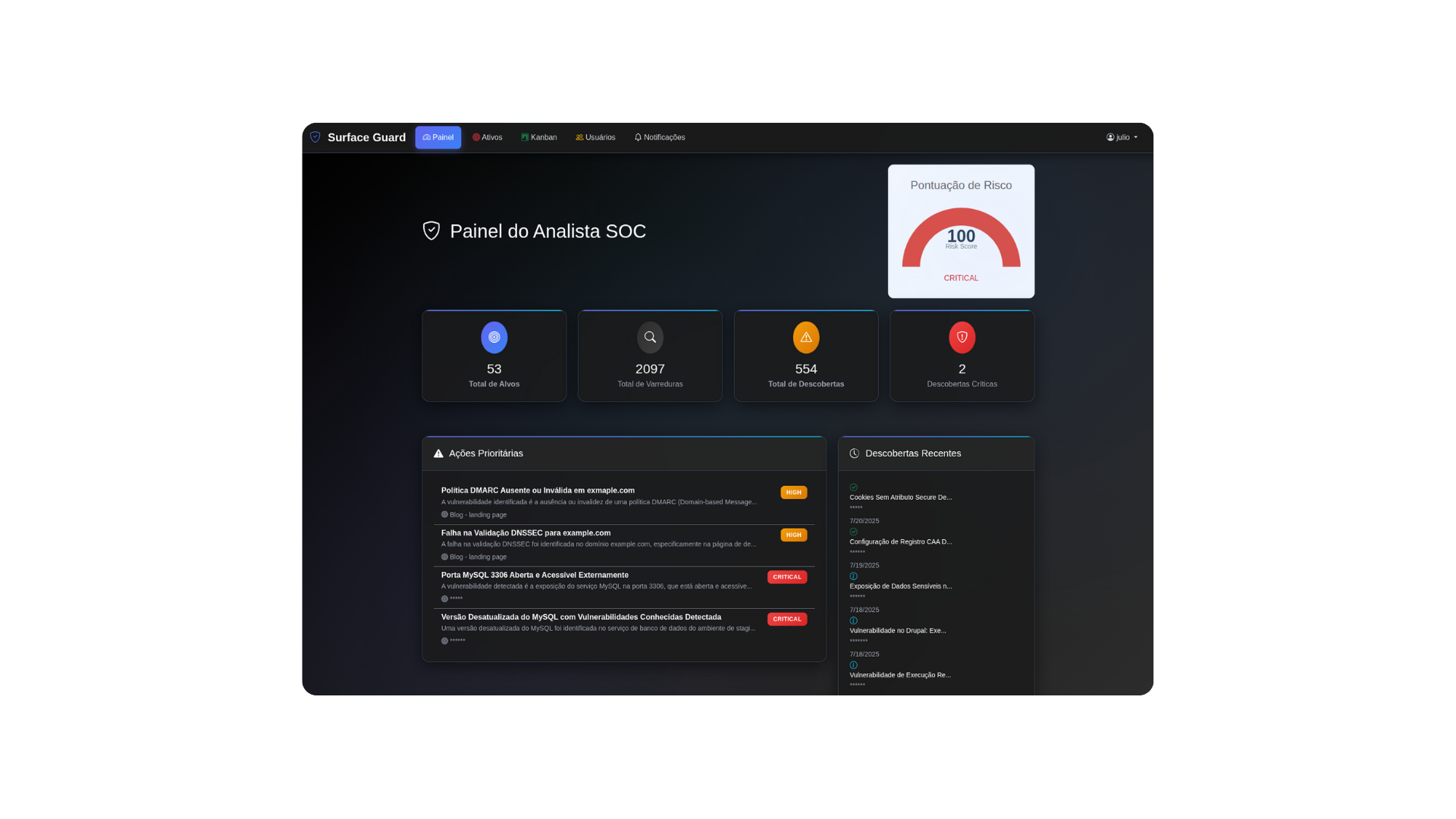
Discover the Surface Guard
The tool Bob used to transform the security of your company
Continuous Monitoring
24/7 scanning of your entire external attack surface, automatically discovering new assets.
Artificial Intelligence
Advanced AI that identifies patterns, ranks risks, and suggests priority actions.
Intuitive Dashboard
Clear and objective visualisation of all risks, without complex technical jargon.